What is the driving force behind a systematic security testing approach?
Let us imagine you are driving your car at 100 mph and suddenly BOOM…!! Out of the blue, the airbags explode in your face causing you life-threatening injuries. Or your pacemaker is tweaked remotely to administer high electrical shocks which could prove to be a silent death.
This is the potential of a cyberattack! Hackers could cause such deadly havocs not only in the automotive or health care industries, but also damages in finance, logistics, telecommunication, and power utilities, to name a few. This calls for a robust automotive-centric security testing methodology.
Connectivity: The open door for hackers
The reason for the hacker’s widespread prominence is the massive connectivity of embedded systems to the outside world. The embedded IoT devices are the heart of all industries and every one of them contains wireless interfaces like Wi-Fi, Bluetooth, NFC, RFID, GPS etc. The more the connectivity and complexity of the software, the larger the attack surfaces for the hackers to penetrate the system and cause harm.
The convergence of the IT world with that of the embedded world on one hand improves the lifestyle of mankind. On the other hand, it is a playground for black-hat hackers and likewise a battlefield for security experts! To win this war against sophisticated, intelligent hackers, we need a real-world verification and validation security hardening mechanism, which is applied across the life cycle of the product.
So here comes the most anticipated question: What is the secret behind good security testing? How can we be as intelligent as hackers?
Security testing as a process
There is no one silver bullet or an elixir that is going to address all the security vulnerabilities…You need a combination of all! Typically, security testing starts with unit testing, then comes static code analysis focusing on the code-related errors. Then we advance to more robust and dedicated techniques like fuzzing, side-channel analysis. Finally, we perform an acceptance test with the penetration test.
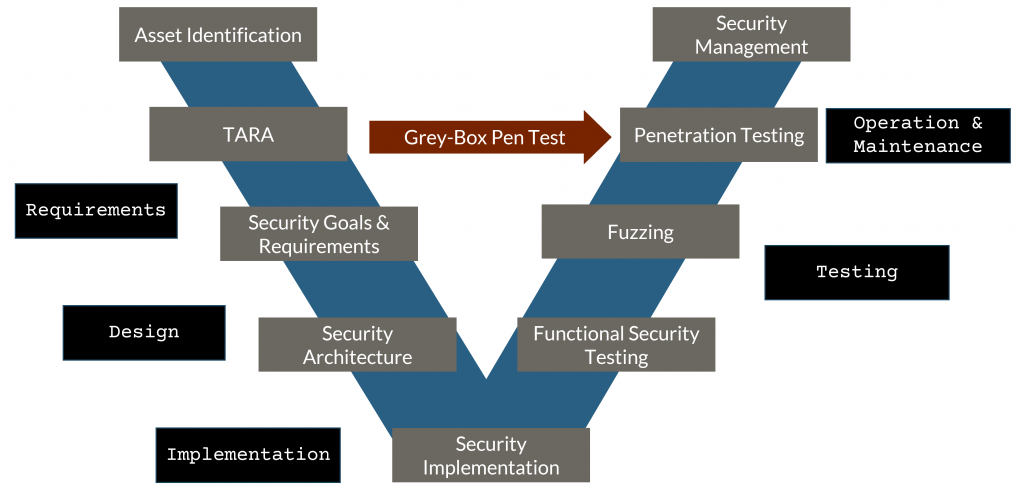
The penetration test or pen test captures certain types of security weaknesses like unintended user action and associated architecture flaws more effectively than others. We all are aware that the penetration test is a late-cycle activity with a huge resource crunch and time constraints… We need a focused testing approach. Risk-oriented grey-box penetration test solves such an issue.
Security testing using grey-box penetration tests
The grey-box penetration test is like the black-box pen test, where the system is treated from the outside. However, in this case, the tester has high-level architecture knowledge and carries out the pen test based on acquired experiences and architecture-specific heuristics. This makes the grey-box pen test an intelligent security testing mechanism. Here at Vector, we perform a systematic and thorough Threat Analysis and Risk Assessment (TARA) at the concept phase and utilize its output in carrying out our novel grey-box penetration testing.
So, in a nutshell: ‘Risk-oriented security with dedicated test methods and tools is the need of the hour!’
There is no safety without security
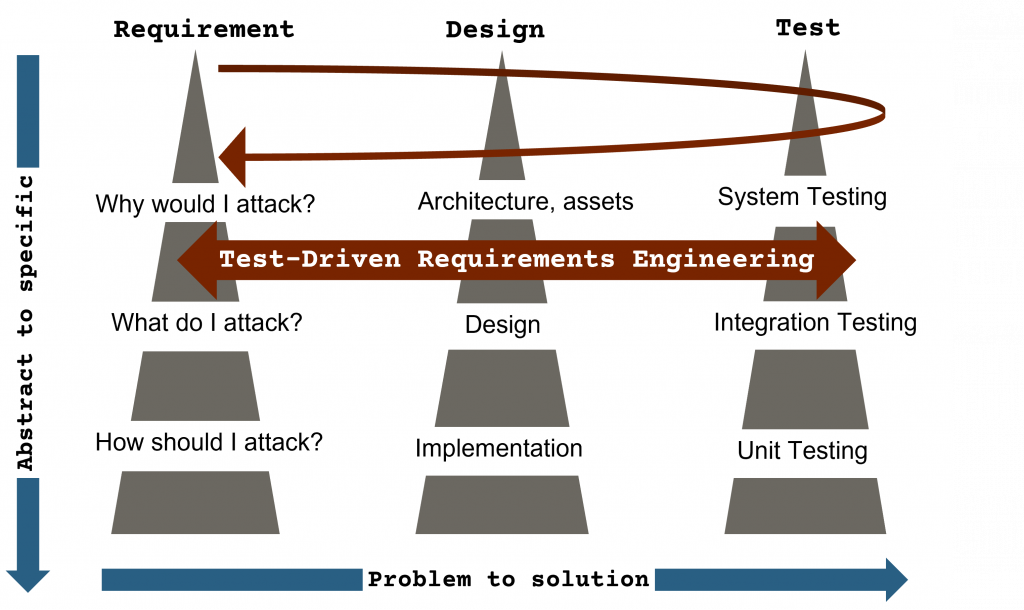
The safety-critical subsystems are ever-increasing in the automotive industry. We cannot guarantee safety unless and until we ensure security. All the security gaps of a system need to be identified. This is possible only if the requirements are well tested. System engineering concepts such as the Triple Peak Model combine requirement analysis, solution modeling and Test-Driven Requirements Engineering. The byproduct of this mechanism is a systematic traceability method and regression testing which are key to any good security testing.
In essence, the grey-box approach provides several advantages such as:
- Risk-based testing with a tailored and thus efficient grey-box methodology
- Easy to understand, asset-related results with a clear structure
- Prioritized list of findings based on the impact categories
Security testing tools make the tester’s life easier
Hmm, this is true but how to select which tools are adequate for the given security activity? In short, how to select the right security tool to give us the results we are looking for?
We must understand the strengths and weaknesses of every tool. There is a variety of tools available in the market such as open-source, commercial tools, fully automated and software as a service.
Examine the tools as per the quality attributes as follows:
- Usability: To make sure the vulnerabilities and related information is reported in a user-friendly readable format with an interactive GUI is a plus point.
- Scalability: To scale up the tool to support different programming languages, network and application protocols. It should also support multiple hardware and software platforms.
- Availability: To make threat library, multi-vector testing capabilities and updated vulnerability databases available to the testers with an easy-to-procure and affordable license cost.
A combination of a good test methodology and the right tool is a win-win situation. As rightly said by the famous American software engineer, developer of Unified Modelling Language (UML), Grady Booch – ‘A fool with a tool is still a fool!’ A tool is merely a means of executing a set algorithm. The heart of a good security testing mechanism lies in its methodology. However, this is not in any way downgrading the importance of a good tool! No way… as automated tools are the means to provide the foreseeable security vulnerabilities in record time!
So, the gist is this game-changer of a test method: Vector Consulting provides a risk-oriented grey-box pen test that supports you as a penetration tester to effectively and efficiently identify an exhaustive list of security gaps with the least amount of test effort.
More information
Vector Consulting brings its years of experience in security testing by focusing on a security-by-lifecycle approach. That is both effective and efficient in exhaustively identifying all security vulnerabilities with the least amount of test effort. We developed our own pen test lab that can be used to independently and efficiently conduct penetration tests for our customers.
Webpage: Risk-oriented grey-box penetration test
IEEE download: Test-Driven Requirements Engineering
Application: Cybersecurity and Penetration Testing for Medical Systems









2 thoughts on “Security testing techniques to combat cybercrime”
The main purpose of penetration testing is to proactively identify and address security vulnerabilities before cybercriminals can exploit them.
Penetration testing can simulate real-world cyberattacks, helping organizations test their incident response plans and procedures.